Exeter’s No.1 Ransomware Data Recovery and Forensic Investigation Specialists
With 25 years of expertise in digital forensics and data recovery, Exeter Data Recovery offers advanced ransomware recovery services tailored to clients across the UK. Our Forensic Investigation Lab is equipped to handle complex cases involving ransomware-encrypted data on laptops, desktops, external storage, and enterprise RAID systems. Whether your organisation is dealing with total encryption, partial corruption, or system lockdown, our forensic methodologies provide a pathway to recovering your critical data.
Our Ransomware Recovery Services
We address a wide spectrum of ransomware infections and scenarios, providing technical investigation and data recovery through a structured, forensic-based approach.
Ransomware Types We Handle
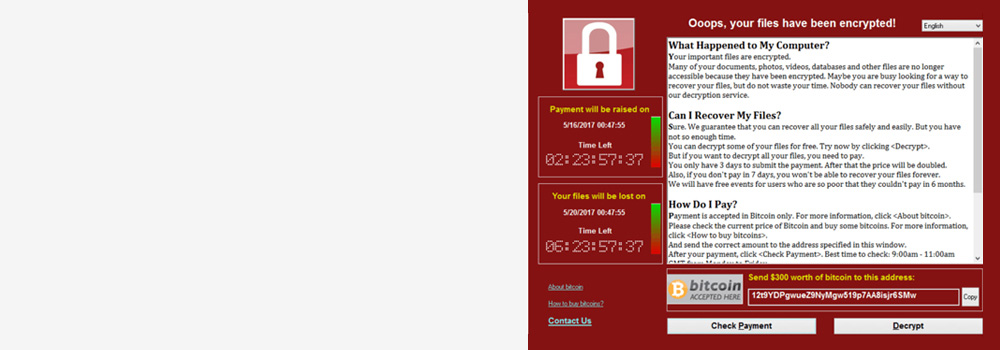
- Common and Advanced Variants: Including WannaCry, LockBit, REvil (Sodinokibi), Dharma, Conti, BlackCat, and more.
- Encryption Algorithms: AES, RSA, Salsa20, ChaCha20 and hybrid encryption structures.
- Targeted File Systems: NTFS, FAT32, exFAT, HFS+, APFS, EXT3/4, XFS, ReFS, ZFS.
Technical Recovery Process for Ransomware-Infected Devices
Each recovery is tailored to the attack type, device configuration, and encryption method. Below are key techniques we employ during ransomware data recovery:
1. Ransomware Variant Identification
- Process: Using digital signatures, header analysis, and encrypted file extensions, we determine the exact ransomware strain.
- Purpose: Enables matching known decryption keys or exploiting known flaws in the malware.
2. Decryption Tool Deployment
- Process: We apply verified decryption tools when available for specific ransomware variants.
- Purpose: Recover files with minimal data loss, preserving folder structure and file integrity.
3. Brute Force and Key Search
- Process: We perform brute-force attacks on weak encryption implementations or search for leaked keys through forensic analysis of RAM dumps and shadowed memory areas.
- Purpose: Useful for recovering data from outdated or poorly coded ransomware.
4. Partial File Reconstruction
- Process: In cases of partial encryption, unencrypted data fragments are analysed and reconstructed using binary comparison and header repair tools.
- Purpose: Restore partially affected files such as documents, spreadsheets, and media files.
5. Shadow Copy and Volume Snapshot Recovery
- Process: We scan for intact Windows Volume Shadow Copies (VSS) or hidden system restore points.
- Purpose: Restore earlier versions of files or system states prior to the attack.
6. File Carving from Unallocated Sectors
- Process: Deep scan of the drive’s unallocated space to recover deleted or hidden file remnants using file signature recognition.
- Purpose: Recover data that was deleted by the ransomware before or during encryption.
7. Forensic Metadata Reconstruction
- Process: Extract and rebuild file metadata (timestamps, ownership, directory paths) even when the file content is encrypted.
- Purpose: Aid in identifying affected files and reconstructing directory structures post-recovery.
8. Disk Imaging and Preservation
- Process: Sector-level imaging of all infected storage media to protect original data from further damage.
- Purpose: Enables safe recovery from working copies without risking data integrity.
9. RAID-Specific Ransomware Recovery
- Process: In RAID environments, we first rebuild the virtual RAID configuration from disk members before applying ransomware recovery methods.
- Purpose: Ensures full logical reconstruction before tackling encrypted data.
10. Negotiation Support and Analysis
- Process: For extreme cases, we provide forensic assistance in safely contacting threat actors (via third-party legal representatives if applicable).
- Purpose: Used only when other decryption avenues have been exhausted and client-approved.
Supported Devices and Systems
We provide ransomware recovery services for:
- Laptops & Desktops
- External Hard Drives & SSDs
- USB Flash Drives & Memory Cards
- RAID Servers & NAS Systems
- Virtual Machines & Disk Images
- Windows, macOS, Linux & UNIX Systems
Why Choose Exeter Data Recovery?
- 25 Years of Proven Forensic and Data Recovery Experience
- Specialists in Ransomware Encrypted Devices and Storage Systems
- In-House Digital Forensics Lab Based in Exeter
- Custom Recovery Solutions Tailored to Your Threat Scenario
- Support for Legacy and Modern File Systems
- RAID and Server-Level Ransomware Recovery Expertise
- Free Diagnostic Assessment and Detailed Forensic Reporting
Contact Our Forensic Ransomware Team
If your data is encrypted due to a ransomware attack, do not reboot, reinstall, or attempt recovery using free tools—these actions may make recovery impossible.
Contact Exeter Data Recovery for a free diagnostic consultation. Our ransomware specialists will assess your system, identify the strain, and present the safest and most effective recovery options.